Yes. Security Policy Manager integrates seamlessly with iManage Work 10 in the Cloud.
See it in action

Advanced access controls
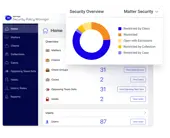
With Security Policy Manager access controls, you can manage user access — and delegate access approval responsibility — at the client, function, or project level, and across any organizational structure or global location.
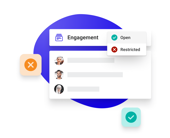
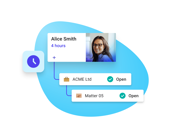
Self-maintaining rules
Driven by automated workflows, Security Policy Manager lets you configure self-maintaining policies that grant and revoke access automatically. This reduces both the burden and the risks of manual intervention.
Single-policy management
Maintain a consistent security posture with Security Policy Manager by protecting content stored across multiple repositories that include iManage Work and third-party systems, through the application of a single policy.


Extensive auditing
Respond quickly to the most rigorous client or regulatory audits using the comprehensive auditing capabilities on Security Policy Manager dashboards. Customize and enforce security settings that follow Outside Counsel Guidelines (OCG) and other client mandates.
Work integration
Security Policy Manager has a unique integration with iManage Work that ensures you can establish, adjust, and remove security policies without access control cascades, document re-files, or content re-indexing — and with no performance impact to end users in iManage Work.
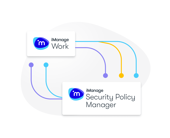

Platform integration
Seamless integration with the iManage platform means Security Policy Manager can flag access details in iManage Work, Conflicts Manager, and Records Manager. Software agents enable it to integrate with third-party applications like common network file shares, Microsoft SharePoint and Teams, and time and billing systems.
Video case studies

Cole, Scott & Kissane puts employees at the heart of innovation

Click, migrate, start working
FAQs
Can’t find the answer to your question? Book a call with our team for a personalized demo or consultation.
Is Security Policy Manager in the Cloud?
Is there a separate cost for Security Policy Manager?
Security Policy Manager may already be included in your Work Cloud subscription. Please consult with your iManage Account Executive.
Does Security Policy Manager support mobile devices?
Yes. Security policies can be managed and reviewed on mobile devices.
Can we use Security Policy Manager together with Threat Manager?
Yes. By combining both products with the native security provided by iManage Work, organizations can benefit from comprehensive security to close the loop on insider and external threats.
Is Security Policy Manager a tool for IT?
Not necessarily. Security Policy Manager can be used by central IT teams as well as small legal departments or organizations with no IT staff.
How easy is it to run Security Policy Manager?
The intuitive interface in Security Policy Manager enables non-technical staff to create and configure rules once it is implemented.
Resources
Making Knowledge Work
Request a demo
Ready to see how iManage can make a difference to your organization?