How to set a security policy for your entire organization
A security policy establishes guidelines and standard procedures to protect an organization, its operations, and its knowledge and intellectual assets from cyberthreats, both internal and external. While the latter gets the headlines, the former deserves serious concern.
According to one of the most respected annual cyberthreat reports, 18 percent of data breaches in 2021 were internal and 39 percent involved third-party partners. For professional services firms experiencing lateral turnover by job-hopping associates and employees, terminating employees may want to secretly take with them confidential information, which can include intellectual property. This type of theft is common. The large frequency of partner data breaches suggests that a security policy should also cover any members of your business ecosystem with network access.
Generally, a security policy has two parts: technical and organizational. The first, for example, would include network diagrams that show segmentation, the locations of routers and wireless access points, and the names of personnel with administrative and configuration privileges. It could include the firm’s incident response plan, too.
The organizational part of a security policy provides rules governing employee access and use of information, data, and intellectual property that belongs to the firm or to its clients. Typical topics would include: acceptable use of IT infrastructure, applications, and data; access control, including remote access; how to handle sensitive data; proper email protocols; and the use of social media.
To be effective, a security policy must apply to everyone, from leadership and partners to associates to administrative employees. It should explicitly state consequences or penalties for inappropriate use of IT and knowledge assets, either intentionally or inadvertently. But to apply to everyone, the policy must be supported by periodic training and ongoing communication.
Balancing security and accessibility
One important consideration that organizations must evaluate, especially law firms and other providers of professional services, is how to balance security and accessibility. These two factors are essential to making knowledge work and, based on our experience with thousands of customers worldwide, they underpin the pain points and successes that iManage customers share.
As illustrated in below, iManage Security Policy Manager can help enact effective knowledge and intellectual property safeguards while supporting appropriate accessibility for relevant stakeholders. Although designed for law firms and corporate legal departments, its features and capabilities can benefit many other professional service providers as well as organizations in a wide range of industries.
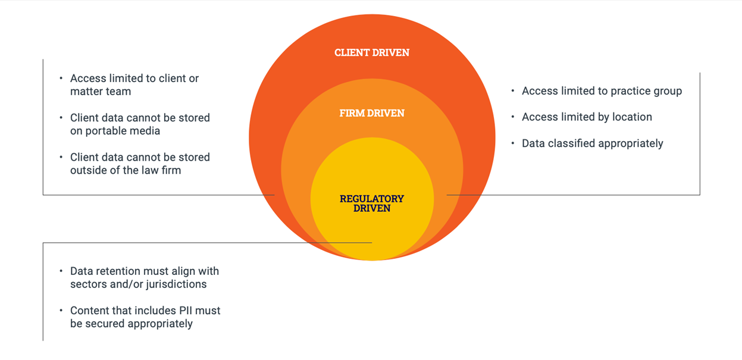
Ensuring secure, cross-business knowledge sharing
Sharing knowledge easily yet securely across your organization can break down silos and facilitate greater collaboration, which can lead to better business outcomes. For law firms, security must support the entire legal document lifecycle, too, including creation, management, legal hold, records retention, and disposition.
To overcome organizational resistance to adoption, security must be unobtrusive and as transparent as possible. Security must ensure ease of use, mobile and remote access on any device, and compliance with broad, quickly evolving regulatory changes.
Modern organizations need systems that provide high security but give more granular access controls and flexibility than the open or closed options that can either risk too much or inhibit workflow.
Find out more about securing your knowledge and sensitive data while balancing protections and accessibility; Protect knowledge and secure your vision.





Manuel Sanchez is Information Security & Compliance Specialist at iManage with extensive professional experience in information security, governance, and compliance.