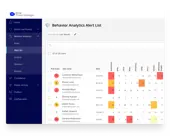
Yes. iManage Threat Manager integrates seamlessly with iManage Work in the Cloud.
Advanced threat detection
State-of-the-art machine learning and powerful advanced forensics enable iManage Threat Manager to ensure rapid detection, investigation, and neutralization of a malicious attack.


Reduce false positives
Threat Manager analyzes both usage patterns and context information i.e. client, matters, peer groups to reduce false positives that overburden staff and generate threat alerts that have a high probability of being legitimate.
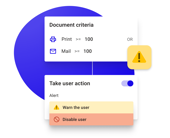
Smart alerts
Custom actions can be defined in Threat Manager, including alerting a user or supervisor, escalating to a manager, or disabling an account based on the severity of a threat.
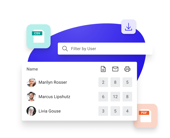
Compliance reporting
Organizations can easily share clients how their sensitive information is managed and protected by using Threat Manager and show regulatory bodies how the application’s extensive reporting capabilities enable them to meet applicable compliance requirements.
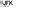
Accurate notifications
Granular reporting across multiple entities delivers visibility into the access and flow of sensitive data. Organizations can monitor user behavior and adoption to detect anomalous activities and quantify the risk of data that isn’t properly filed.

SIEM support
Integration with SIEM (Security Information and Event Management) tools enables organizations to gain enhanced visibility into malicious activity in iManage Work and see Threat Manager alerts in their SIEM application of choice.
Case Studies
Watch Threat Manager in action.
Cole, Scott & Kissane puts employees at the heart of innovation

Cole, Scott & Kissane puts employees at the heart of innovation
Actionable insights ward off threats

Actionable insights ward off threats
Every knowledge-based organization faces the challenge of protecting sensitive information from the menace of cybercrime. Learn how Travers Smith safeguards its precious knowledge assets — and those of its clients — with iManage.
FAQs
Can’t find the answer to your question? Book a call with our team for a personalized demo or consultation.
Is Threat Manager available in the Cloud?
Is there a separate cost for Threat Manager?
Threat Manager may already be included in your iManage Cloud subscription. Please consult with your iManage Account Executive.
Can we use Threat Manager together with Security Policy Manager?
Yes. By combining both products with the native security provided by iManage Work, organizations can benefit from comprehensive security to close the loop on insider and external threats.
Is Threat Manager a tool for IT?
Threat Manager is used by central IT teams as well as organizations with no IT staff.
How easy is it to run Threat Manager?
The intuitive interface enables non-technical staff to create rules and export reports from iManage Threat Manager after it is implemented.
Resources
Making Knowledge Work
Request a demo
Ready to see how iManage can make a difference to your organization?